#90daysofdevops-Day-67: AWS S3 Bucket Creation and Management through Terraform
AWS S3 Bucket
Amazon S3 (Simple Storage Service) is an object storage service that offers industry-leading scalability, data availability, security, and performance. It can be used for a variety of use cases, such as storing and retrieving data, hosting static websites, and more.
In this task, you will learn how to create and manage S3 buckets in AWS.
Task: Hands-On
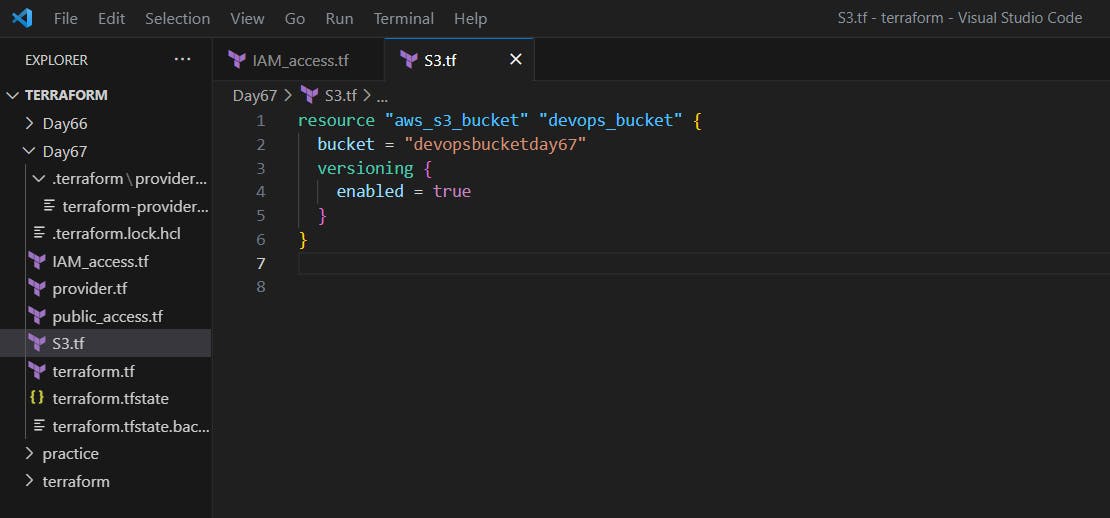
Create an S3 bucket using Terraform
resource "aws_s3_bucket" "devops_bucket" { bucket = "devopsbucketday67" }Create an S3.tf with required bucket name.
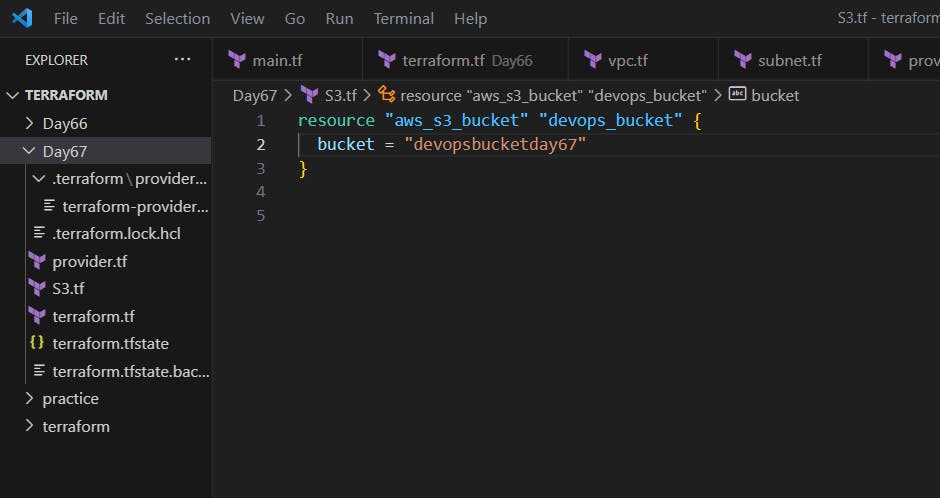
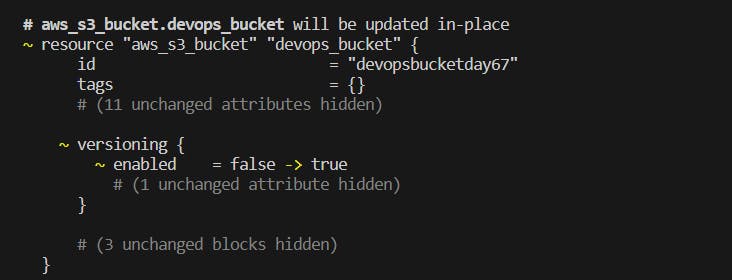
Use terraform init and plan to get the providers and view the terraform changes.
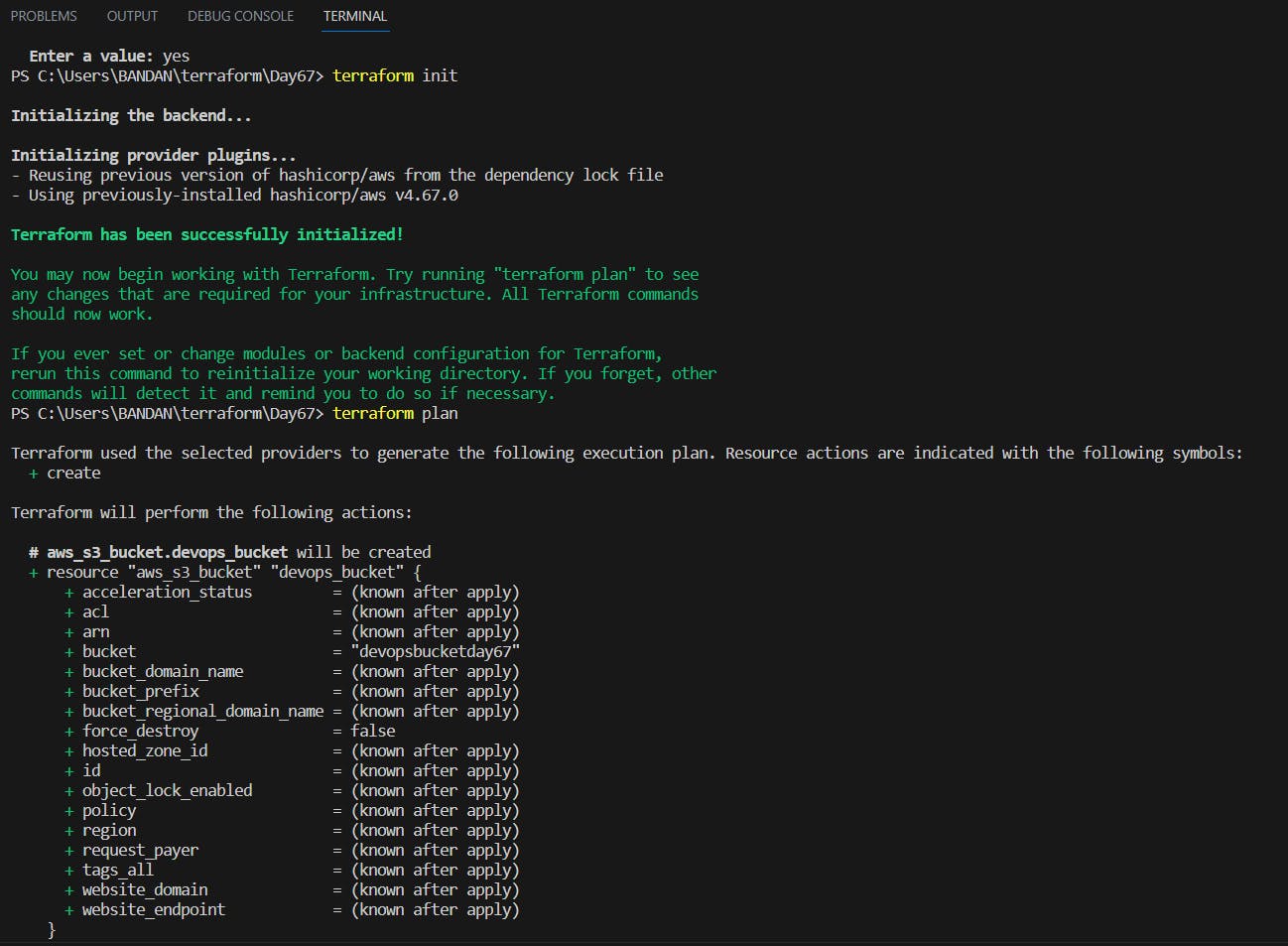
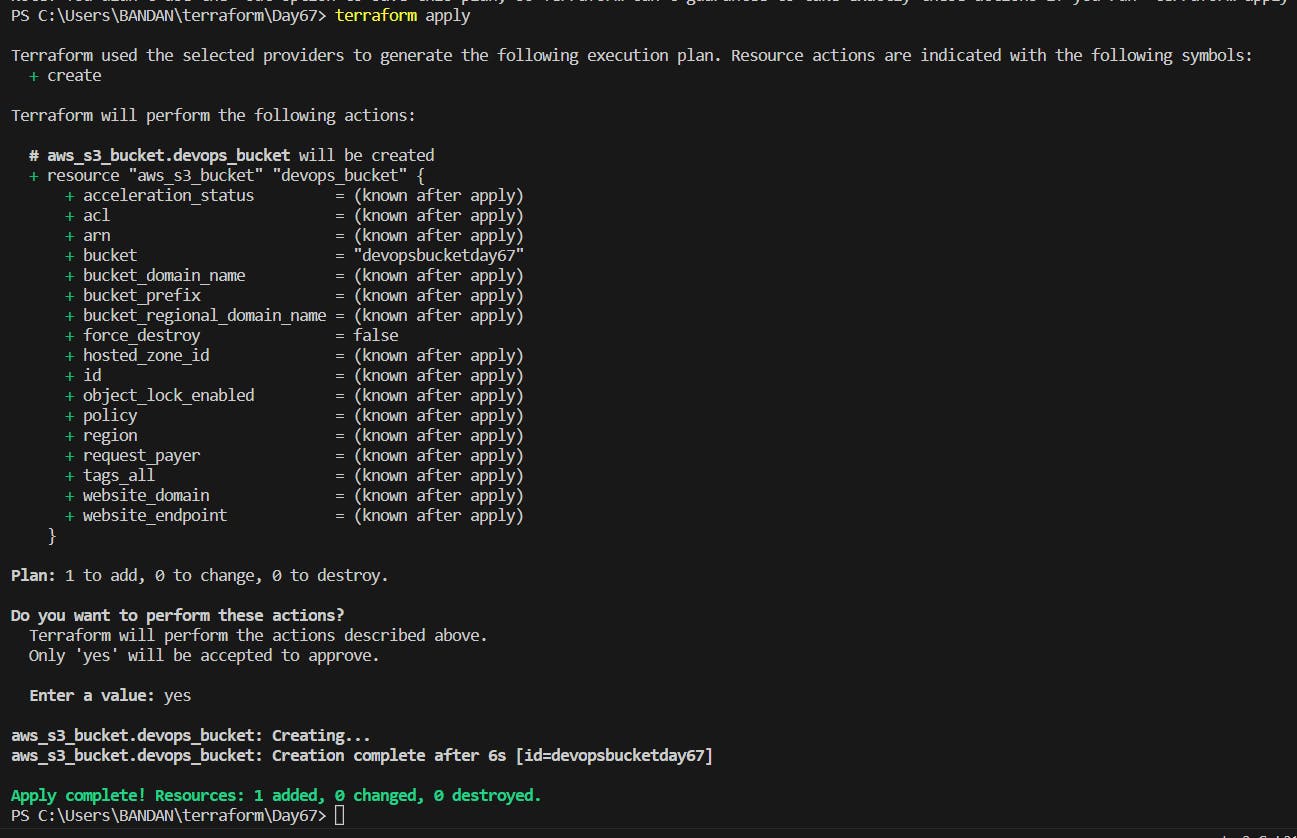
Now, use terraform apply to make the changes using terraform files.
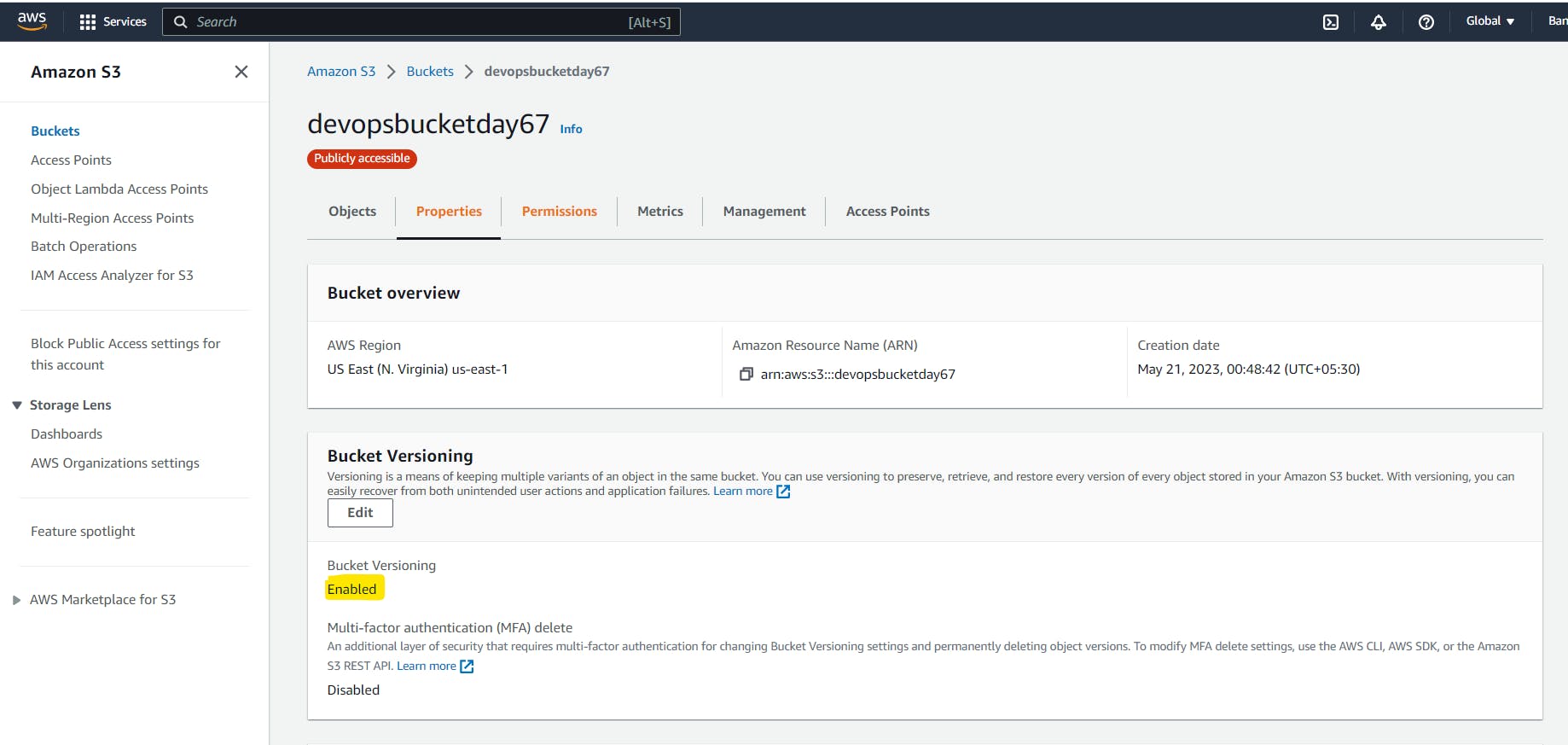
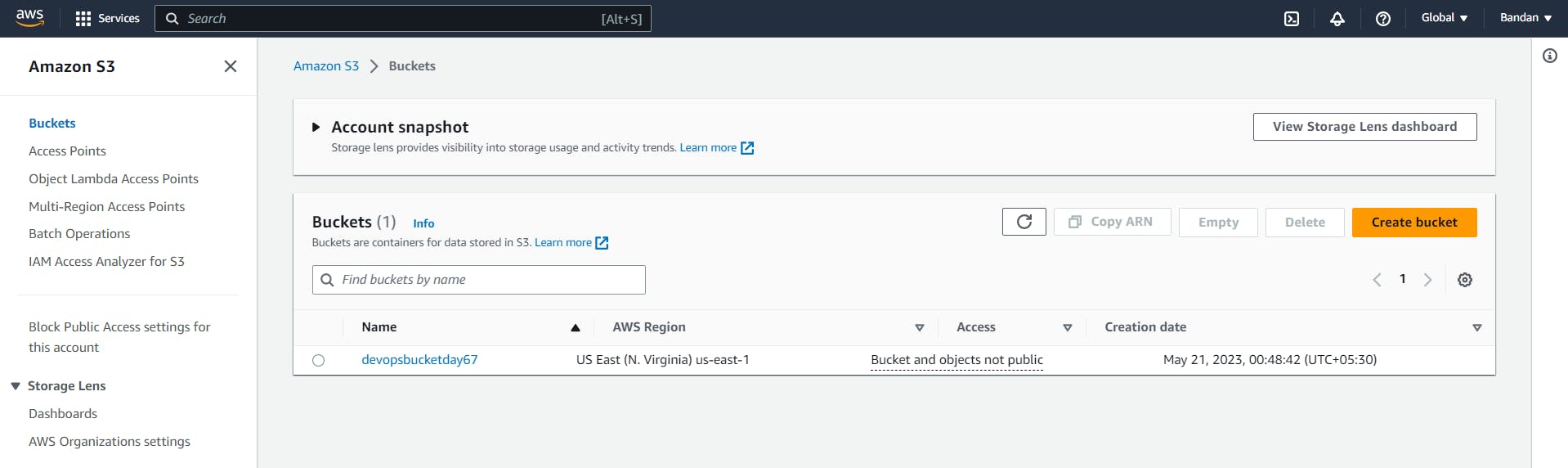
Navigate to the AWS management console and go to S3 to view the bucket created.
Configure the bucket to allow public read access
resource "aws_s3_bucket_public_access_block" "example" { bucket = aws_s3_bucket.devops_bucket.id block_public_acls = false block_public_policy = false ignore_public_acls = false restrict_public_buckets = false } resource "aws_s3_bucket_acl" "bucket_acl" { bucket = aws_s3_bucket.devops_bucket.id acl = "public-read" }Enable the ACL in the S3 bucket and choose Bucket owner preferred and save the change.
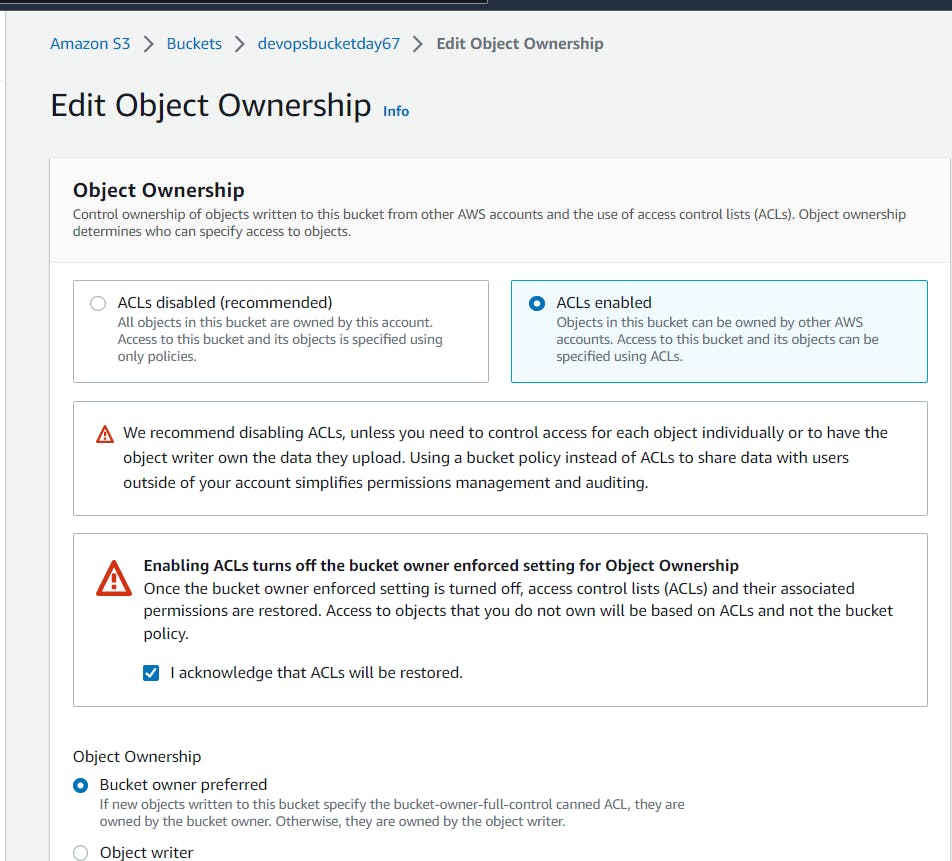
Create a public_access.tf file and write proper configuration.
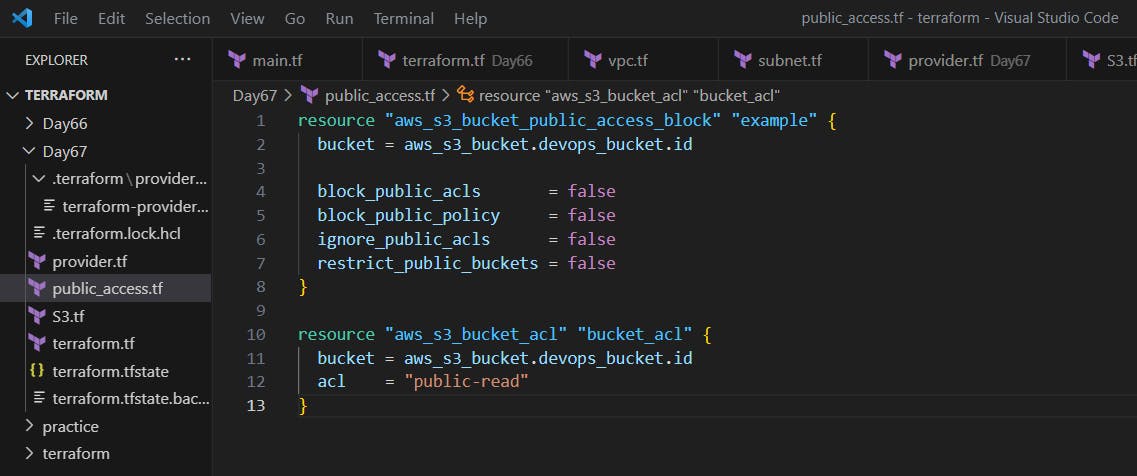
Use terraform apply to create public access for the S3 bucket.
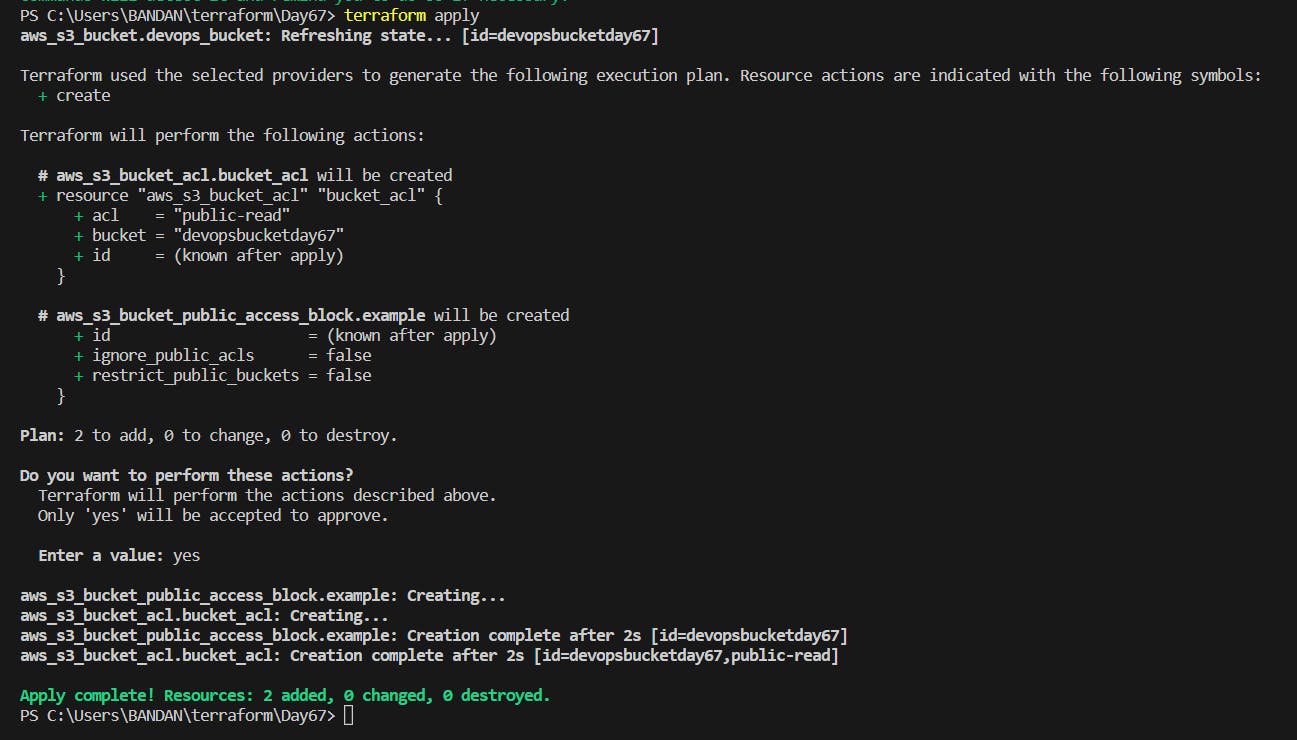
Check the bucket in the console for the public access which is now enabled.
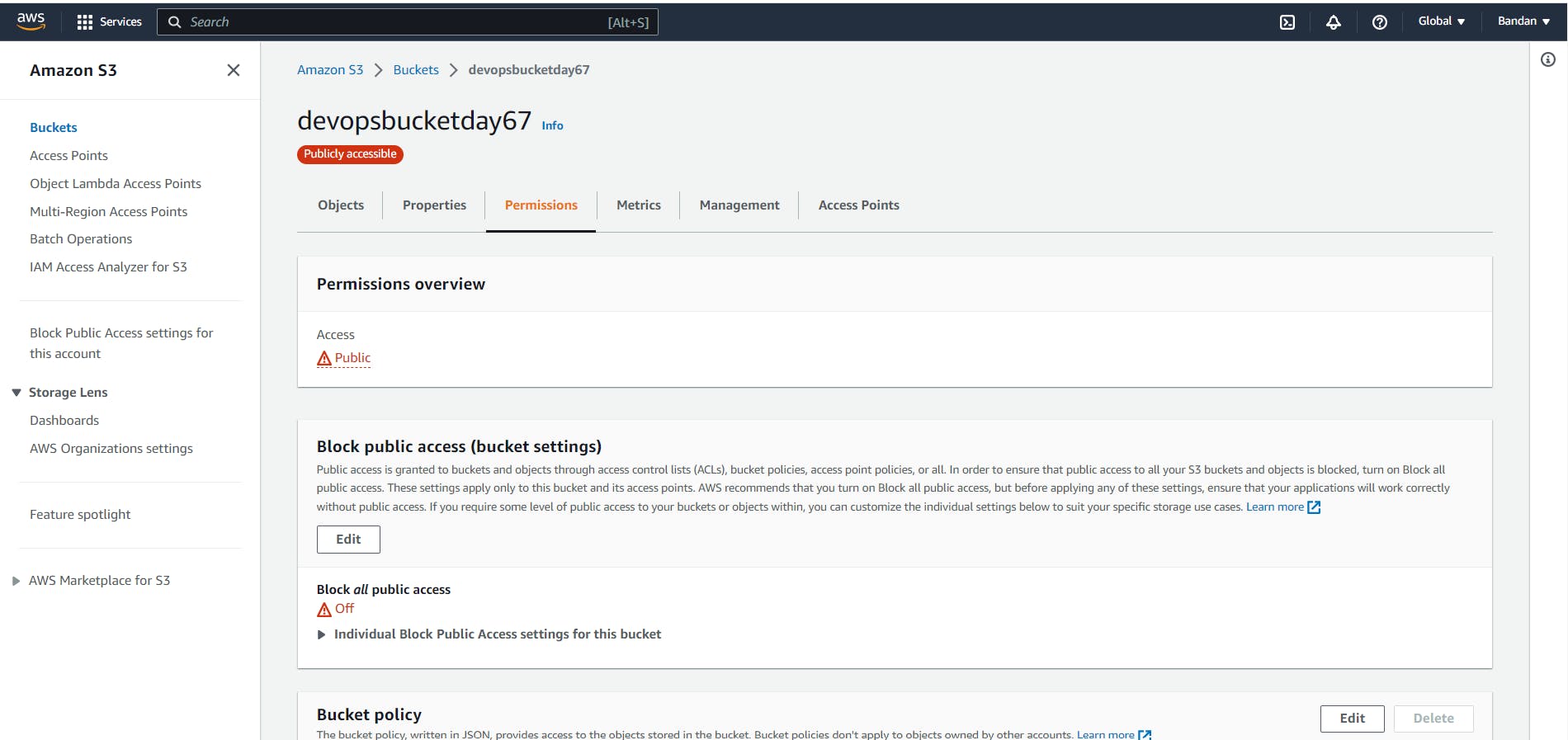
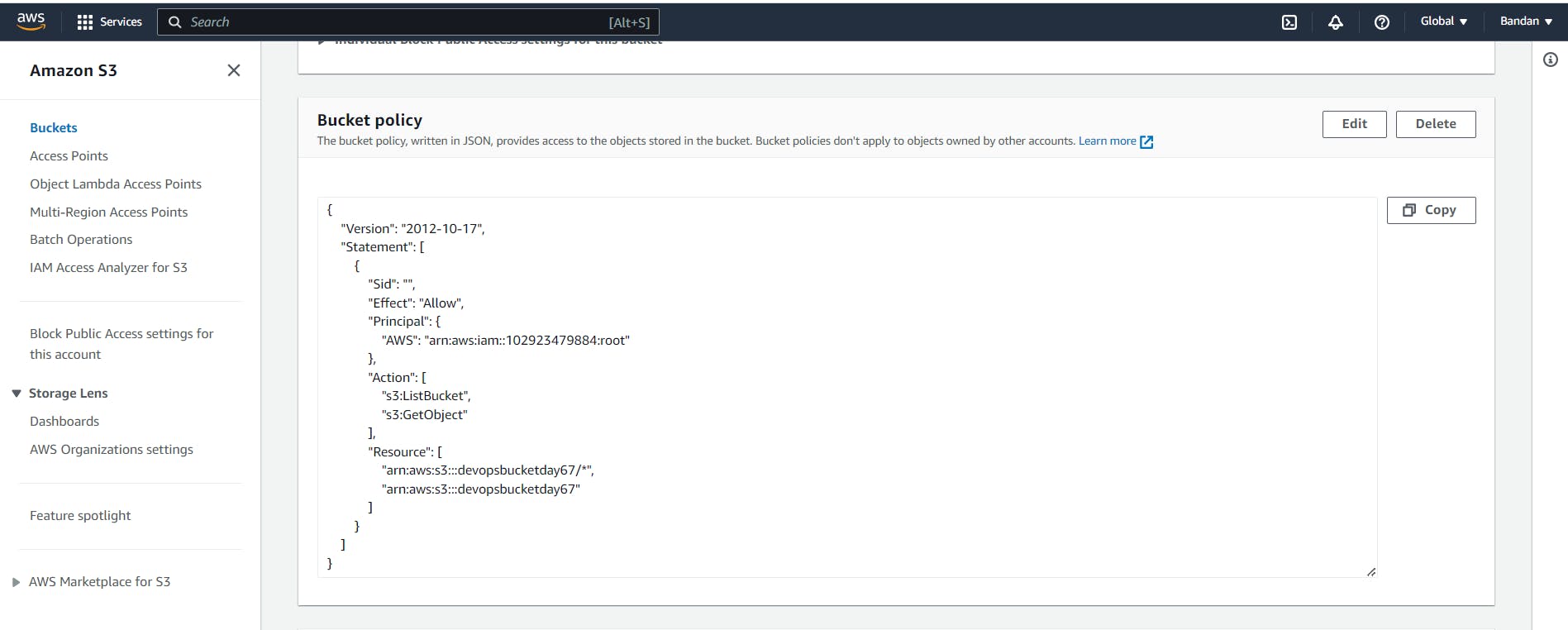
Create an S3 bucket policy that allows read-only access to a specific IAM user or role
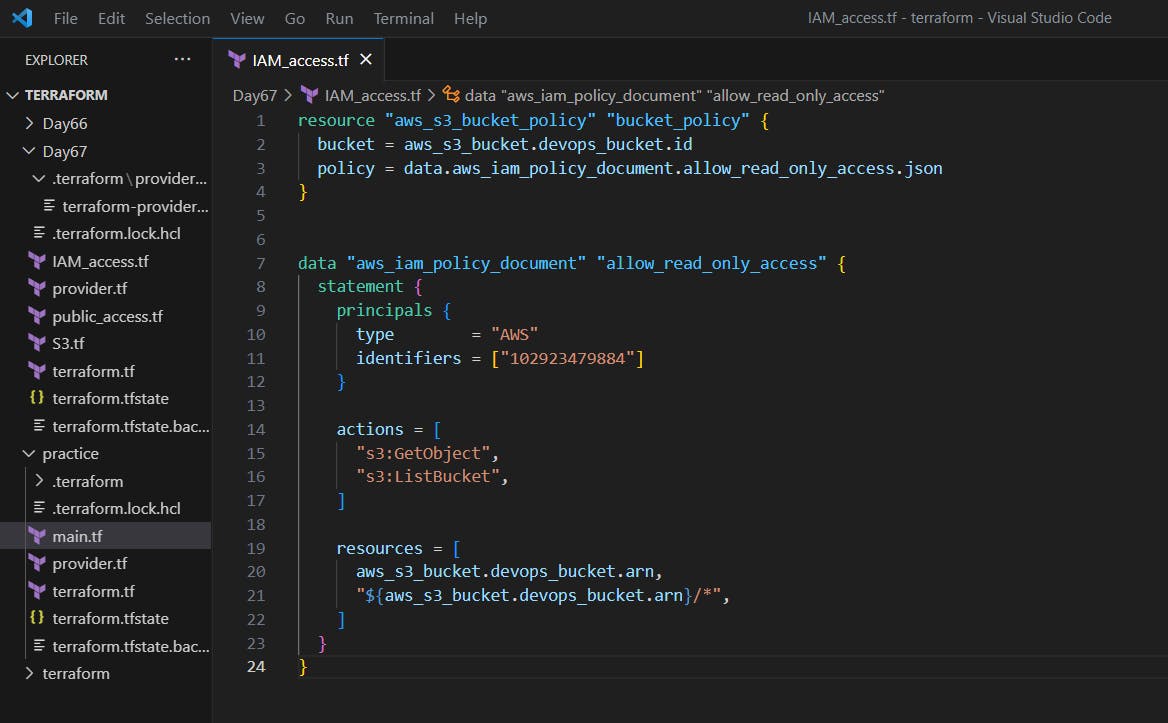
resource "aws_s3_bucket_policy" "bucket_policy" {
bucket = aws_s3_bucket.devops_bucket.id
policy = data.aws_iam_policy_document.allow_read_only_access.json
}
data "aws_iam_policy_document" "allow_read_only_access" {
statement {
principals {
type = "AWS"
identifiers = ["102923479884"]
}
actions = [
"s3:GetObject",
"s3:ListBucket",
]
resources = [
aws_s3_bucket.devops_bucket.arn,
"${aws_s3_bucket.devops_bucket.arn}/*",
]
}
}
Create an IAM.tf file to write the configuration of IAM read access for the S3 bucket.
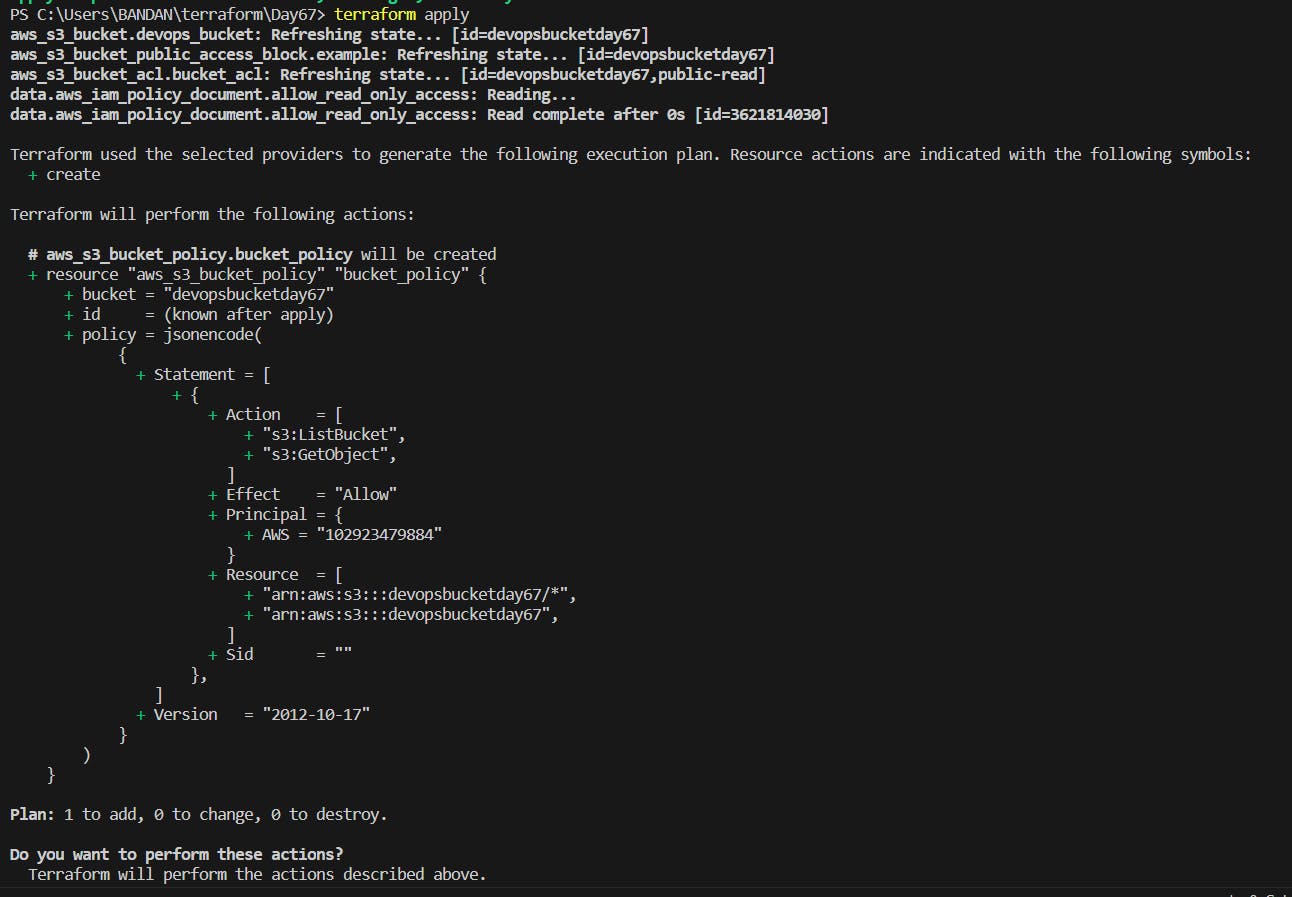
Now, use terraform apply to provide the access in the bucket.
Now, check the bucket to view the policy.